Hi!
I know I’m late to the party, but with the IPv4 exhaustion now being expressed in monetary costs by VPS/Cloud providers, it is time to seek IPv6. My main use-case is to be able to reach servers exclusively over IPv6, so I don’t need to pay for IPv4 assignments if those servers will not serve direct public traffic (i.e.: database, storage and job servers).
My home provider did have IPv6 support, but they pulled the plug in 2020, and now 3 years later, I still don’t have IPv6 access. Let’s fix that today.
I had a brief experience experience with SixXS back in 2013, and I’ve learned the importance of latency for such tunnels (150ms+ is NOT ok), so my only option is tunnelbroker.net, operated by HE.NET, which has a PoP 10ms away from me.
Configuration
I run an EdgeRouter X as my gateway. The configuration is fairly straight forward:
root@edgerouter# show interfaces tunnel tun0
address <Client IPv6 Address>/64
description "HE.NET Tunnel"
encapsulation sit
firewall {
in {
ipv6-name WANv6_IN
}
local {
ipv6-name WANv6_LOCAL
}
}
local-ip <Client IPv4 Address>
multicast disable
remote-ip <Server IPv4 Address>
ttl 255
root@edgerouter# show interfaces switch switch0
address 192.168.1.1/24
address <Routed /64 prefix>::1/64
[...]
root@edgerouter# show protocols static
interface-route6 ::/0 {
next-hop-interface tun0 {
}
}
And the firewall configuration:
root@edgerouter# show firewall ipv6-name
ipv6-name WANv6_IN {
default-action drop
description "WAN to LAN"
enable-default-log
rule 10 {
action accept
description "Allow established/related"
state {
established enable
related enable
}
}
rule 20 {
action drop
description "Drop invalid state"
state {
invalid enable
}
}
rule 30 {
action accept
description "Allow IPv6 ICMP"
protocol ipv6-icmp
}
}
ipv6-name WANv6_LOCAL {
default-action drop
description "WAN to Router"
enable-default-log
rule 10 {
action accept
description "Allow established/related"
state {
established enable
related enable
}
}
rule 20 {
action drop
description "Drop invalid state"
state {
invalid enable
}
}
rule 30 {
action accept
description "Allow IPv6 ICMP"
protocol ipv6-icmp
}
}
The values for the items between brackets are to be obtained from the tunnel details page on tunnelbroker.net.
Notably missing from the configuration is DHCPv6, Prefix Delegation and Route Advertisement. I decided to not allow for auto-configuration in my network, but rather manually configure the machines I want with IPv6. Here’s why:
Caveats
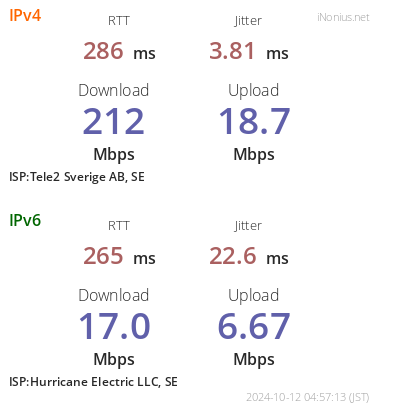
The HE.NET tunnel works. I’m able to reach servers via SSH, HTTP and other protocols just fine. Speed isn’t great, but given it’s a free service, I can’t complain.
A tangential observation: fast.com and speedtest.net both couldn’t test the speed correctly. fast.com used GeoIP to infer my location (sending all the requests from Stockholm to Los Angeles, because HE.NET GeoIP locations). ipv6.speedtest.net sent requests to dual-stack hostnames, so some of the packets did not go through the tunnel.
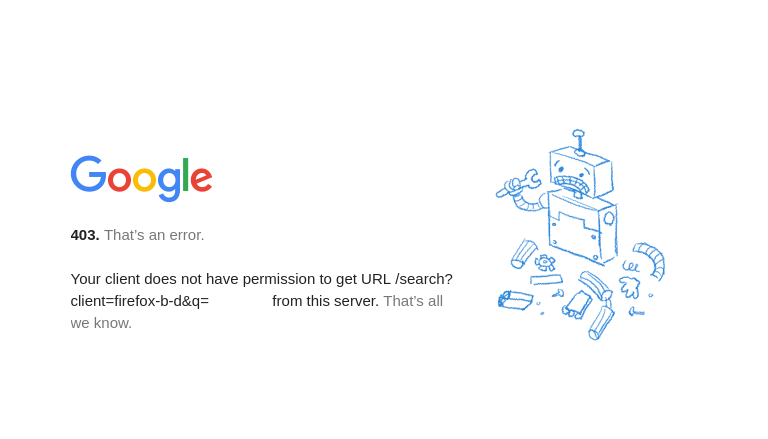
However, free things are prone to abuse, and the HE.NET tunnel is no different, having fell into despair on the wide internet. This can be translated as CAPTCHAs everywhere and Google simply refusing to serve any request coming from their IP range:
I’ve looked into getting a IPv6 PI Assignment from RIPE NCC, but HE.NET charges a $500 setup fee for new BGP sessions, not to mention the LIR sponsorship costs, so it quickly becomes too expensive compared to renting IPv4s from VPS/Cloud providers.
Lastly, HE.NET only supports SIT/GRE tunnels, which don’t work behind CGNAT. If you are behind CGNAT, look for WireGuard tunnels as an alternative.
Outro
I’m happy with the HE.NET service. It fixes my problem and the limitations are manageable for now. If you are in a similar situation and is looking for a IPv6 tunnel, tunnelbroker.services has a small list of IPv6 tunnel services. Alternatively, if you just need IPv6 to test an HTTP endpoint, a SOCKS proxy with ssh -D 1337 your-ipv6-enabled-vps is often enough.
Thank you.